Managing multiple premises with an army of employees is a tedious process, while configuring and updating various devices is yet another daunting task. Through our world acclaimed solutions, you can seamlessly manage thousands of systems with the next generation of firewall using a single platform. It combines application control, sophisticated prevention terminology along with innovative intrusion prevention system (IPS) into easy to implement solution.
Learn More About Our SECURITY
Because in this "bring your innovative side world" managing your business and living up to the advance changes that occur in agile operations of the firm can be challenging. But, you will never have to worry about it anymore when you have the specialized services of Beta Technologies by your side.
Offering a new approach towards security, we help you overcome modern threats in the system so that your business operates smoothly without any complications. Our Network Security driven solutions are based on the framework of Multi-Layer Collaborative Security. This is a holistic model that renders participation of security engines so that together they can be the future of information defense. We deploy certified and advance technologies of highest level so that your company never compromises with the security of its information.
ADVANCE SECURITY PRODUCTS
FOR YOUR SECURITY
We combine the expertise of our professionals with the advance and trustworthy products to protect various network end points, data and network infrastructure. For this, we rely on the major networking solutions like:
This one of a kind solution constantly monitors and immediately blocks the programs that have a suspicious behavior such as exploiting vulnerabilities, memory access and key logging in real-time. It maintains high-standard security environment for those subjects that are often prone to threats including sales terminals and operational technology.
The data security is a comprehensive suite for data encryption and device because it protects data of any kind in any form- in the shared cloud servers, on devices, internal team or shared with business partners. A crucial element of SDS is the effective tools meant to safeguard confidential information, customer data, intellectual property and employee data while keeping an alignment with security and workflow, ensuring productivity never slows down.
When it comes to data protection, Beta Technologies brings to you advance and trusted data protection services to reduce vulnerabilities to network attacks and insider threats. Secure every information of your organization, right from e-mails, web and more, while simultaneously performing various business operations at extreme ease. This means now you can gain visibility and at the same time control the user behavior to protect the much-needed confidential data.
Stolen credentials, hijacked system or unintentional actions of
employees, these are some of the situations that can turn out to
be a company's worst nightmare. But, you can protect the
valuable information using our unraveled visibility insider threat
data protection (ITDP) services and solutions. ITDP integrates
the movement of every data with behavior of the user to ensure
100% secure and effective data protection.
Our data protection solution allows you to bid adieu to those
days when you had to struggle with a myriad of channels only
to protect the data servers, mails and other critical business
information. We take advantage of the most comprehensive
ITDP solution in order to overcome breaches and keep the data
systems safe.
-
NETWORK ATTACK PROTECTION
 We believe that in the present era, enterprises have evolved to be more decentralized than ever. This increases the demand of reliable and consistent security policies across the corporate offices, headquarters, and branches, corporate locations, divisions, remote channels and even home office, as each one of them are crucial for the development of your business.
We believe that in the present era, enterprises have evolved to be more decentralized than ever. This increases the demand of reliable and consistent security policies across the corporate offices, headquarters, and branches, corporate locations, divisions, remote channels and even home office, as each one of them are crucial for the development of your business.
Managing multiple premises with an army of employees is a tedious process, while configuring and updating various devices is yet another daunting task. Through our world acclaimed solutions, you can seamlessly manage thousands of systems with the next generation of firewall using a single platform. It combines application control, sophisticated prevention terminology along with innovative intrusion prevention system (IPS) into easy to implement solution.MULTILEVEL SECURITY
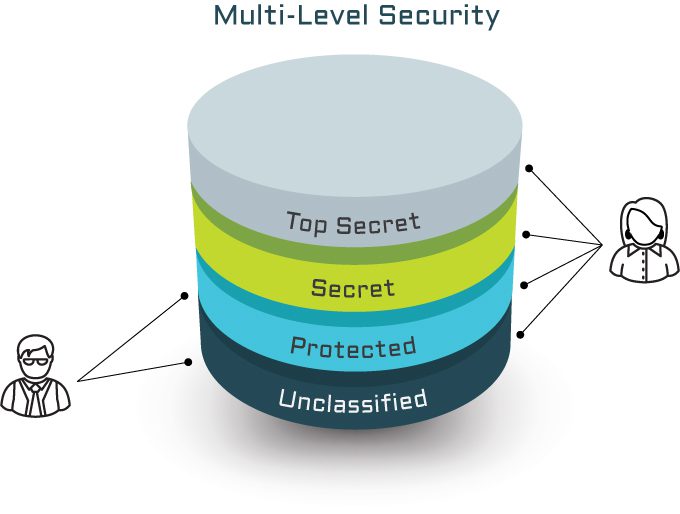 Meant for the physical separation of various networks, Multilevel Security (MLS) is beneficial to secure various components of a data network. This technology gets its origin from the intelligence and defense communities. It can be set according to the varying degree of data securities using a network segmentation model.
Meant for the physical separation of various networks, Multilevel Security (MLS) is beneficial to secure various components of a data network. This technology gets its origin from the intelligence and defense communities. It can be set according to the varying degree of data securities using a network segmentation model.DEMONSTRATE, ACHIEVE AND BECOME A SECURED ORGANIZATION
 Our teams of professionals are known for their years of experience and intuitive approach towards the ever changing demands of cyber security. To serve you with the best, we feature two most promising data security solutions, which are:
Our teams of professionals are known for their years of experience and intuitive approach towards the ever changing demands of cyber security. To serve you with the best, we feature two most promising data security solutions, which are:


